Cipher Triage
Rapid triage with a streamlined, no-fuss approach
Rapidly identify illicit content—such as malware, CSAM, user profiles, and contacts—on Windows systems, whether in the field or the lab. With automated insights and a user-friendly interface, Magnet Outrider empowers both investigators and non-technical users to make fast, confident decisions.
CipherTriage Dashboard
Real-Time Visibility. Instant Insights. Total Control.
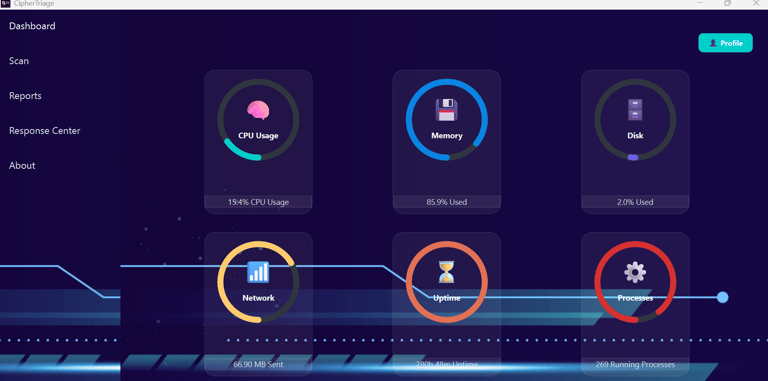
Welcome to the CipherTriage Dashboard — your command center for system diagnostics, incident response, and proactive monitoring. Designed with simplicity and speed in mind, our interface offers a crystal-clear snapshot of critical system metrics, including:
CPU Usage – Track real-time processor load and optimize performance.
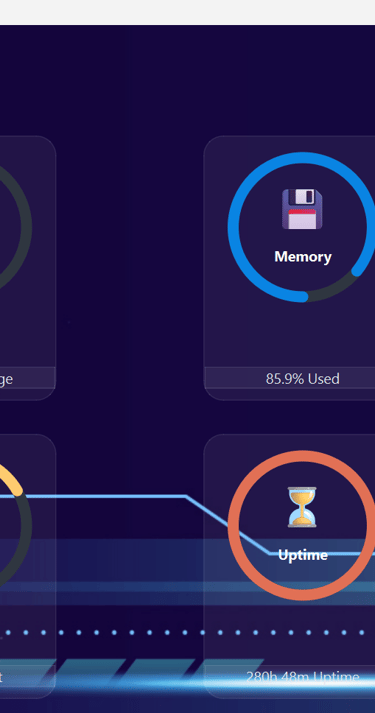
Memory Monitoring – See how much memory is being used and prevent resource exhaustion.
Disk Utilization – Keep storage usage in check to avoid bottlenecks.
Network Traffic – Analyze data flow to detect unusual patterns or breaches.
Uptime Tracking – Monitor system stability and availability with precision.
Running Processes – Gain full visibility into active tasks and potential anomalies.
CipherTriage empowers your security and IT teams to detect, analyze, and respond to issues before they escalate. It’s more than a dashboard —it’s your frontline defense.
Identify actionable evidence fast
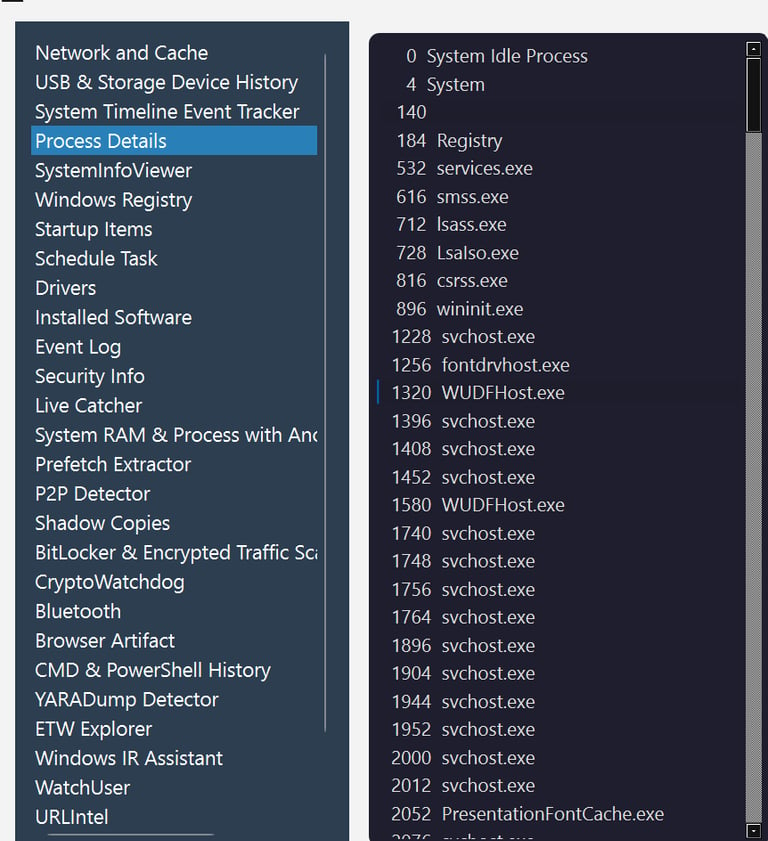
Artifact is a powerful all-in-one forensic analysis toolkit designed for speed, depth, and precision. With over 30 specialized modules, investigators can rapidly analyze system processes, registry changes, network activity, external devices, and more—all through an intuitive, streamlined interface. Whether you're tracking malware, uncovering remote access, or correlating system events, Artifact delivers fast, actionable insights for both field and lab environments.
P2P Detector & Network Surveillance
Expose Hidden Connections. Eliminate Stealth Threats.
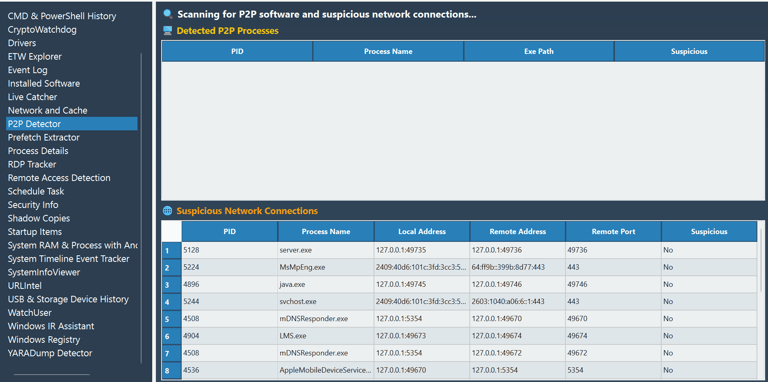
Our P2P Detector module empowers cybersecurity teams with the ability to identify unauthorized peer-to-peer software, analyze suspicious network activity, and flag stealthy exfiltration channels before they become incidents.
P2P Software Detection
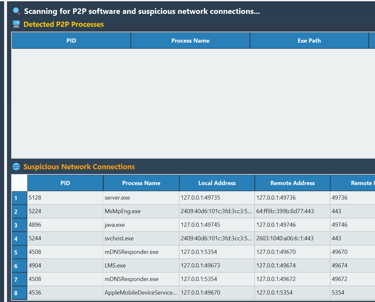
Uncover hidden or rogue applications that use decentralized communication to bypass security controls.Suspicious Network Connections
Monitor process-level network behavior, correlate local and remote addresses, ports, and detect anomalies—even from localhost or loopback traffic.Context-Rich Insights
Each process is mapped with PID, executable path, and behavioral suspicion scoring to provide clear, actionable data—no guesswork.Zero Trust Compatible
Ideal for threat hunting, insider threat analysis, and Zero Trust network enforcement.
Whether you're auditing a system or responding to a breach, CipherTriage gives you the visibility and granularity required to see what attackers don’t want you to see.
Network and Cache Monitor
Uncover Stealthy Connections. Gain Deep Network Visibility.
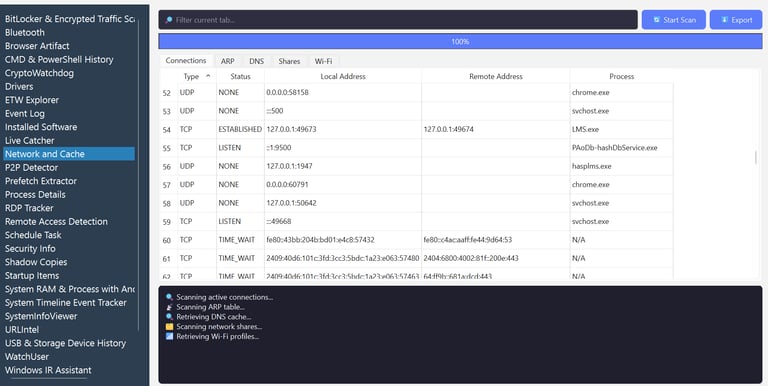
The Network and Cache module is your forensic-grade lens into live network activity and cached data. Designed for incident responders and threat hunters, this tool enables real-time inspection of:
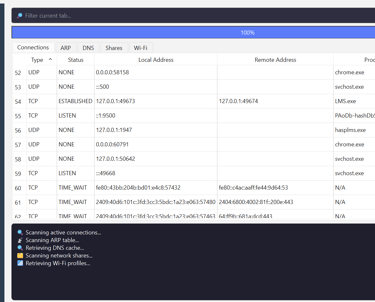
Active Network Connections
Monitor every TCP and UDP connection, including local and remote addresses, ports, and associated processes — ideal for detecting suspicious or hidden communications.ARP and DNS Cache Analysis
Track resolved hosts and IP mappings to reconstruct attacker movement or DNS poisoning attempts.Network Shares & Wi-Fi Profiles
Identify open network shares and saved Wi-Fi connections, crucial for tracing lateral movement and past access points.Live Filtering & Export Support
Filter tabular data in real-time and export full reports for documentation or deep analysis.
Whether you're dealing with an APT or internal compromise, CipherTriage empowers analysts to map the entire digital footprint, in just a few clicks.
Products
Expert cybersecurity and forensics for your business.
Resources
© 2025. All rights reserved.
Note : Most of the Products and Services offered by us are meant for Government, Defence and Law Enforcement Organisations and are required to be used in Ethical manner for National Interest. Usage of Products should be as per the Local Government Regulation/ Norms.