Cipher CaseOne
Cipher CaseOne is a powerful desktop-based Incident Response (IR) case management tool designed for digital forensics and cybersecurity teams. Built with an intuitive interface, it eliminates the chaos of the traditional "Spreadsheet of Doom" by centralizing your investigative workflows in one seamless environment.
Case Management, Reimagined
Built on the Familiar – Supercharged for Efficiency
CaseOne leverages the power and simplicity of the traditional spreadsheet—often dubbed the Spreadsheet of Doom—to create a powerful, yet familiar, investigative workspace. All case data is retained within the spreadsheet itself, ensuring easy distribution and collaboration, even outside the application.
Multi-User Collaboration
Enable seamless teamwork across your team. Case files can be stored locally or on shared network drives, allowing multiple investigators to work in parallel. With built-in file locking, CaseOne ensures secure, conflict-free collaboration.
One-Click Data Sanitization
Sharing just got simpler. With a single click, CaseOne sanitizes sensitive indicators like domains, URLs, IP addresses, and more—making it safe to share files with external parties or store them securely without manual redaction.
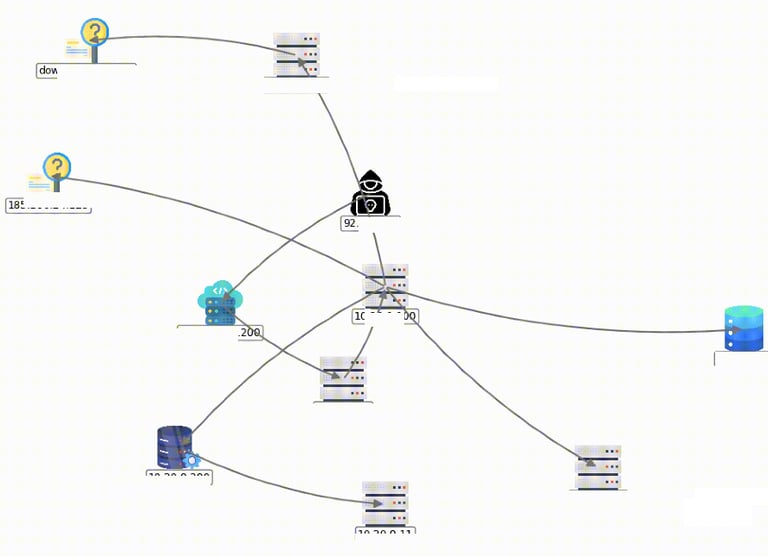
Data Visualization That Tells the Story
Attack Chain Visualization
Uncover the adversary’s movement with clarity. CaseOne’s dynamic Attack Chain Visualization presents lateral movement across your environment, offering a clear picture of how the incident unfolded. Multiple layout modes ensure flexibility in how you view and interpret the data.
Incident Timeline
Quickly grasp the full narrative of the incident. The interactive timeline arranges events in precise chronological order, enabling investigators to analyze actions, delays, and escalation patterns at a glance.
Seamless Export for Reporting
Visuals that speak for themselves. Whether you're preparing a briefing or documenting findings, CaseOne lets you export both the Attack Chain and Incident Timeline as high-quality images or structured CSV files—ready for use in reports, presentations, or evidence submission.
Integrated Threat Intelligence Lookups
IP Reputation & Metadata
Quickly assess any IP address with enriched threat intelligence, including reputation scoring, geolocation, open ports, known vulnerabilities, and more—powered by seamless API integrations.
Gain insights into domains and URLs through WHOIS data, DNS records, and related threat indicators. Understand the infrastructure behind potential threats instantly.
Identify malicious binaries using hash-based lookups across multiple threat intel platforms. Get insights into malware classification, signatures, and historical behavior.
Domain & URL Intelligence
File Hash Analysis
CVE & Exploit Context
IP Reputation & Metadata
Stay ahead of known threats. CaseOne aggregates vulnerability intelligence—including CISA advisories and major CVE databases—to provide context around exploit activity and affected systems.
Verify if an organization’s data has been leaked or published following a ransomware incident, enabling faster response and communication.
Security Framework Mapping
MITRE ATT&CK Integration
Map observed adversary behaviors directly to the MITRE ATT&CK framework. Stay aligned with industry-standard tactics, techniques, and procedures (TTPs) for enhanced threat context and investigation accuracy.
MITRE D3FEND Mapping
Link identified ATT&CK techniques with corresponding defensive measures using D3FEND. This defender-centric mapping empowers analysts to rapidly identify mitigation strategies and harden systems post-incident.
VERIS Reporting Support
Track and document incidents using the VERIS (Vocabulary for Event Recording and Incident Sharing) schema. Share structured data with government entities and contribute to broader threat intelligence efforts, including the Verizon DBIR.
Products
Expert cybersecurity and forensics for your business.
Resources
© 2025. All rights reserved.
Note : Most of the Products and Services offered by us are meant for Government, Defence and Law Enforcement Organisations and are required to be used in Ethical manner for National Interest. Usage of Products should be as per the Local Government Regulation/ Norms.